 The Cyberthreat
The Cyberthreat
When there is a possible malicious attempt to disrupt or even damage a computer or network system, it can be termed as a Cyber Security. While this is the precise definition found in the Oxford Dictionary, it is largely incomplete without the inclusion of data theft.
Ideally, the threat also includes the attempt of a Cyber Security-infiltrator to access crucial and sensitive files from the network. The adversary gains entry into the system to cause ‘possible’ damage. Sometimes, the threat is identifiable only after the damage has occurred. TTP or Tactics, Techniques, and Procedures may be used to detect such dangers. While Gartner did predict a substantial increase in Information Security Spending over the years, others envisage that it will be more than $101 billion by 202o. That is still lower than what Gartner predicted for 2019 but stands in good stead.
The fact remains that Cyber Security threats are constantly on the rise and enterprises have to safeguard themselves from potentially damaging strategies deployed by miscreants. XCEL Corp formulates some of the best cybersecurity measures customized for every industry and business requirement.
Need for understanding
While IT bodies are constantly warning companies convincing them that cyber threats are real, somehow, still, businesses seem to brush the danger aside as superficial. It is only when wide-scale data breaches are reported that enterprises wake up to the fear of data theft. Then again, if you think that it is only large enterprises that are a target, then you are grossly mistaken. A report submitted by Symantec indicated that in 2015, over 43% of the cyber-attacks were on smaller businesses. The cyber threat is growing relentlessly. Yet there is no conscious and simultaneous defense built by the enterprises. A report subsequently, indicated that only about 14% of the smaller and medium-sized businesses are equipped to fight cyber-attacks effectively, while the rest remain unguarded. Both enterprises and SMBs have to address cybersecurity issues immediately to ascertain business growth technologically and profitably.
Seek good quality advice
When technology is used, your business can benefit multi-fold. But the alerts surrounding cybersecurity have to be addressed mindfully, especially if yours is an information-sensitive business. XCEL Corp’s consultants will provide you with advice by first analyzing the nature of your business and then gauging the type of threats that the enterprise is potentially prone to. Our organization comprises of some of the most brilliant tech minds that will grind out a code to erase all vulnerability. It is always best to work with a cybersecurity professional who will make your operations secure and foster long-term relationships to ensure the scalability, workability, and profitability of your company. We incorporate adequate levels of security to fend off even likely lawsuits if any.
Planning
Companies must strategize and articulate a defense plan along with the cybersecurity professionals to detail the measures that will be undertaken so that all networks and employees stay protected from these threats. Policy procedures should also outline the steps that employees must take to ensure that the company’s, as well as the clients’ information, stay protected.
XCEL Corp designs a process that outlines tasks to be performed in the event of a cyber-attack. All process strategies are presented in great detail, precisely customized to the industry that your business is involved in. We pay particular attention to the fintech operations of your company and create plans with some underpinnings. Our consultants will also conduct reviews and lay foundations for future continued monitoring as well.
Types of attacks
Phishing
Activated for around 246,231,645 times in 2017 Kaspersky’s Anti-Phishing system recorded more than 91 million triggers in 2017 when compared to 2016. Phishing attacks are also considered as one of the biggest cybersecurity threats today. The breach is meant to steal credit card credentials, user logins, business and financial information and other types of personal data. These are advanced socially engineered attacks that are unfortunately extremely effective and can even penetrate trusted websites, banking institutions, and other secure digital spaces.
Supply chain attack
Software update supply chain attacks saw a surge sometime in 2017 and 2018. A piece of malware is implanted into a legitimate software package where it usually gets distributed. This occurs when you are using a supplier, vendor or third-party to store or redirect your production. Direct control is lost when information is shared compromising the confidentiality, availability, and integrity of the information.
Ransomware
Ransomware attacks happen practically every day. It is of utmost priority to build defenses against ransomware that can potentially lead to permanent data loss due to the infection of encrypted data and secure database systems. Unless a ransom is paid up, then there is a threat to delete files or corrupt them. These require some stringent endpoint security solutions instead of traditional anti-virus packages.
Advanced threats
Information is stolen when an unauthorized attacker code is released into the system, which very tactfully evades detection. This type of attack is known as APT or Advanced Persistent Threat. For a significant period, the code exists inside the network to steal login information, credit card credentials, and other critical security information including patents. APT inserts Malware into an organization’s network through an email, or application vulnerability to compromise the entire network and yet the breach may not be detected. APT infects the deepest parts of a network, thus making it highly impossible to navigate between connections.
Indications, countermeasures, and guidelines
Cybersecurity, by itself, is a vast arena that requires diverse countermeasures and guidelines to address different types of threats. Nevertheless, here are some preventive actions that you can implement.
Use encryption and schedule regular backups
to minimize detrimental outcomes of a potential Cyber Security-attack. Protect your data by employing effective backup and recovery systems and even set up a periodic backup schedule. Test the backup system as well to avoid unprecedented decryption. Check with our experts for backup and encryption requirements.
Phishing threats
are high-tech scams that appear in the form of e-mails. It typically contains several misspellings, inadequate grammar, and even some generic greetings. The attachments are crafted maliciously and the email by itself contains links to another equally malicious site. Many a time, the company even appears legitimate – such as your employer, credit card Company, banking details, or even a payment provider. You are promised a reward or even a dire consequence for not executing what is indicated in the email.
XCEL Corp monitors the receipt of all such suspicious emails, especially asking you to exchange personal and financial information. Alternatively, to ascertain the authenticity of the mail, we look for a digital signature. At any cost, we advise users not to download these files. It is best to delete all such emails that are received.
Outdated software
is a vulnerability that provides adversaries the opportunity to access information from systems. The software makes unauthorized attempts to access the system besides performing software and hardware modifications, data transmission and much more. As a result, the files are corrupted and information from the hard drive is lost. Systems are sabotaged as the hackers access your network.
XCEL Corp admonishes every organization to lay down policies for technology as well. We regularly improve all current patches and perform frequent software updates. Regular computer audits are conducted and intrusion attempts are taken seriously and reported.
XCEL Corp
Even as you evaluate the exposure and the risk of your company to data theft and cyber attacks, you should also know that the danger cannot be ignored. Cyber Security threats can affect businesses of any size and the impact of such an occurrence can have dire consequences. With XCEL Corp, you will have some fantastic resources at your disposal along with a team of experienced professionals waiting to lend a hand along the way.
Check with XCEL Corp’s experts for remedies to all cybersecurity threats and various measures that can be adopted to counter such dangers.

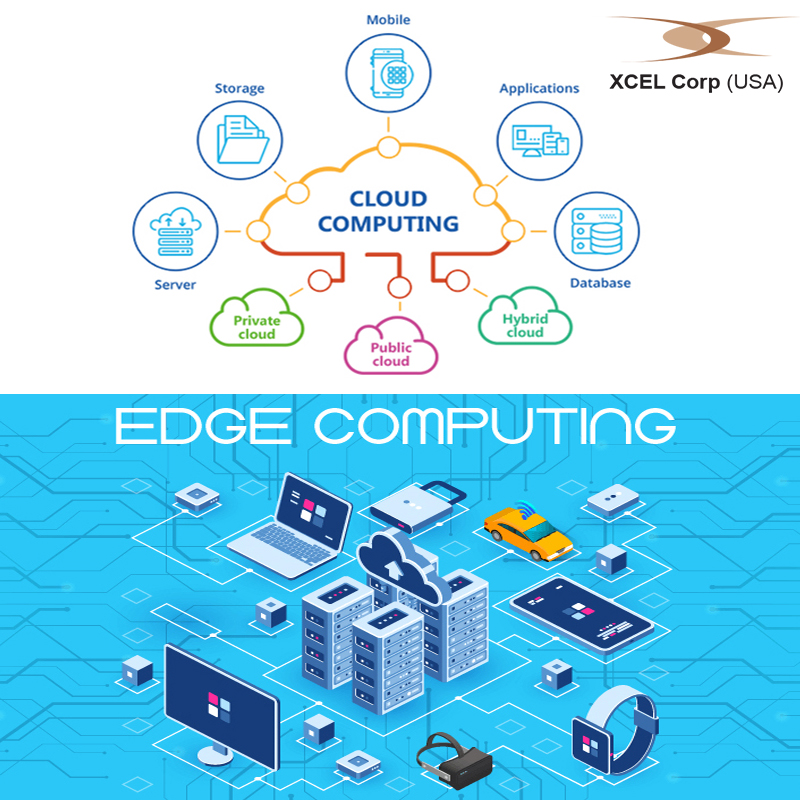 The theory of Edge Computing
The theory of Edge Computing For companies that are looking to migrate to the cloud, AWS remains their top pick. But now with several other providers in the fray,…
For companies that are looking to migrate to the cloud, AWS remains their top pick. But now with several other providers in the fray,…