
A recent news item reported that ultrasonic waves could actually activate Siri. This means the hacker can take pictures, provide commands and read…

A recent news item reported that ultrasonic waves could actually activate Siri. This means the hacker can take pictures, provide commands and read…

The SOC 2 compliance was formulated to successfully discuss an organization’s controls and if they are relevant to the operations that they are undertaking….
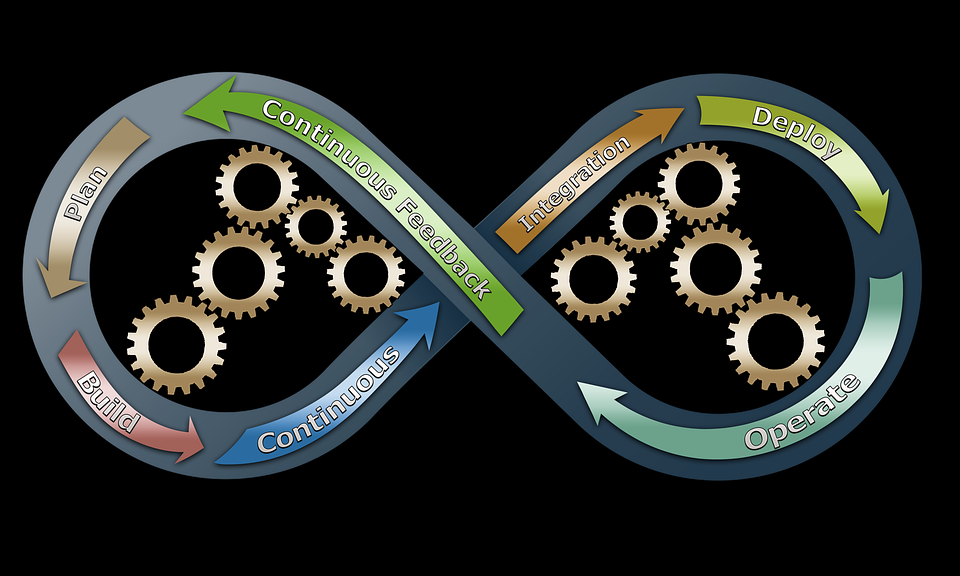 DevOps, as the name suggests, essentially combines development and information technology operations, to save on costs and duration of development. High-quality software is delivered…
DevOps, as the name suggests, essentially combines development and information technology operations, to save on costs and duration of development. High-quality software is delivered…
Most of the time, cryptocurrency, Bitcoin and blockchain are mentioned together. Yet they can be quite confusing for those who don’t know much about it. While these activities and terms are not interchangeable, it…
 Women play an important role in today’s technology. A Harvard review suggests that organizations with no female board member yielded less…
Women play an important role in today’s technology. A Harvard review suggests that organizations with no female board member yielded less…
Network security means to protect your systems against hacking and unauthorized changes of the files in the computer network. It ensures business productivity by assuring the integrity and performance of the firm’s network from…

The bigger the volume of data, the better the insight and the more precise the inference. Companies are fast adopting analytics solutions to improve…
Essentially, a facial recognition technology is used to verify and identify a person’s features on a video source from a digital image or a video frame. There are several approaches…
Android is an open source mobile operating system developed by Google to be used on mobile devices like smart phones and tablets. It is primarily designed for touch screen mobile devices. Google also developed…
Apache Hadoop is a java based open source software framework that makes use of a network of computers for storing and processing massive amounts of data sets. All the modules in Hadoop are…